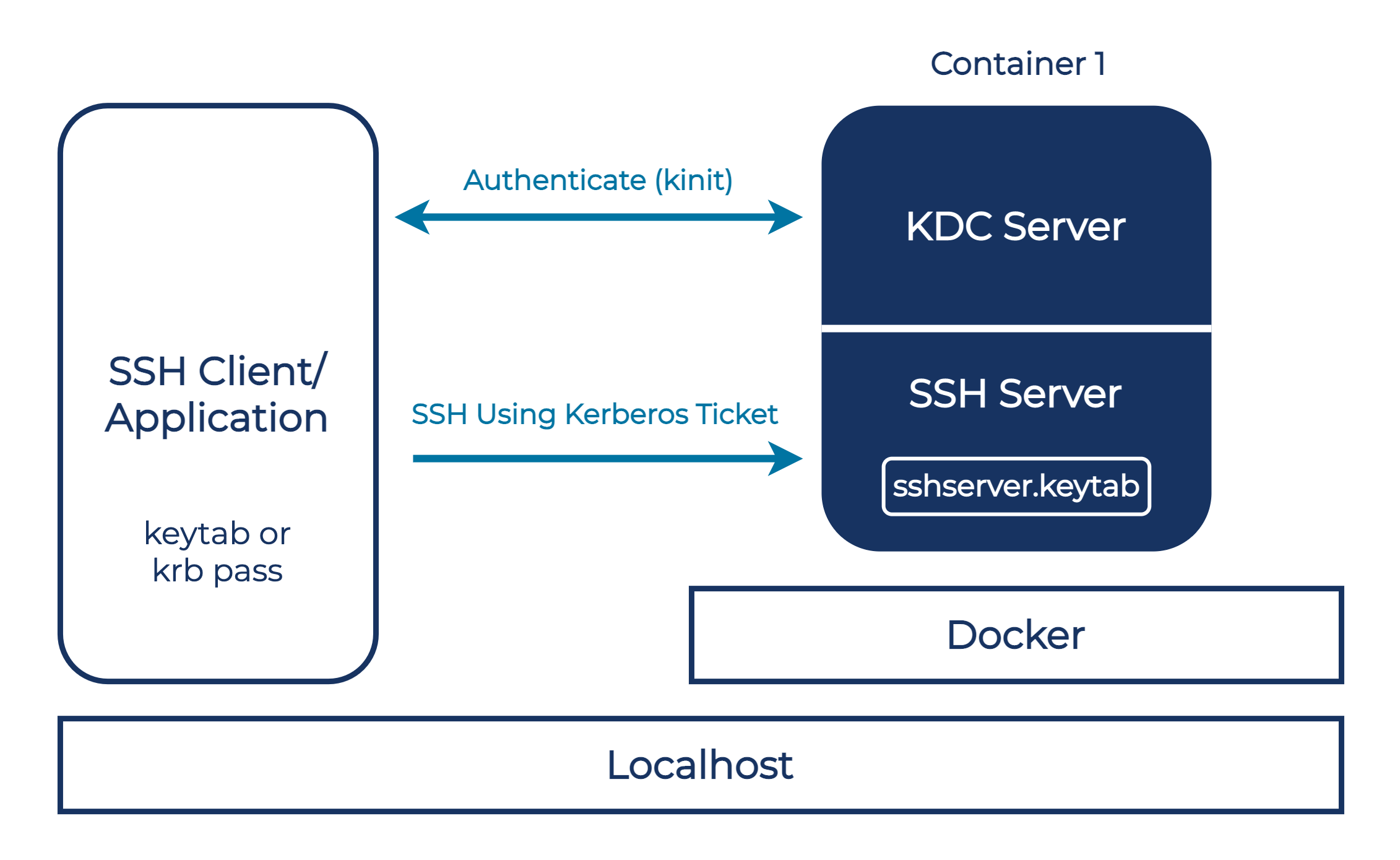
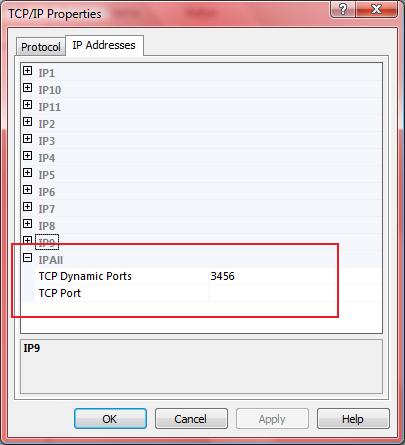
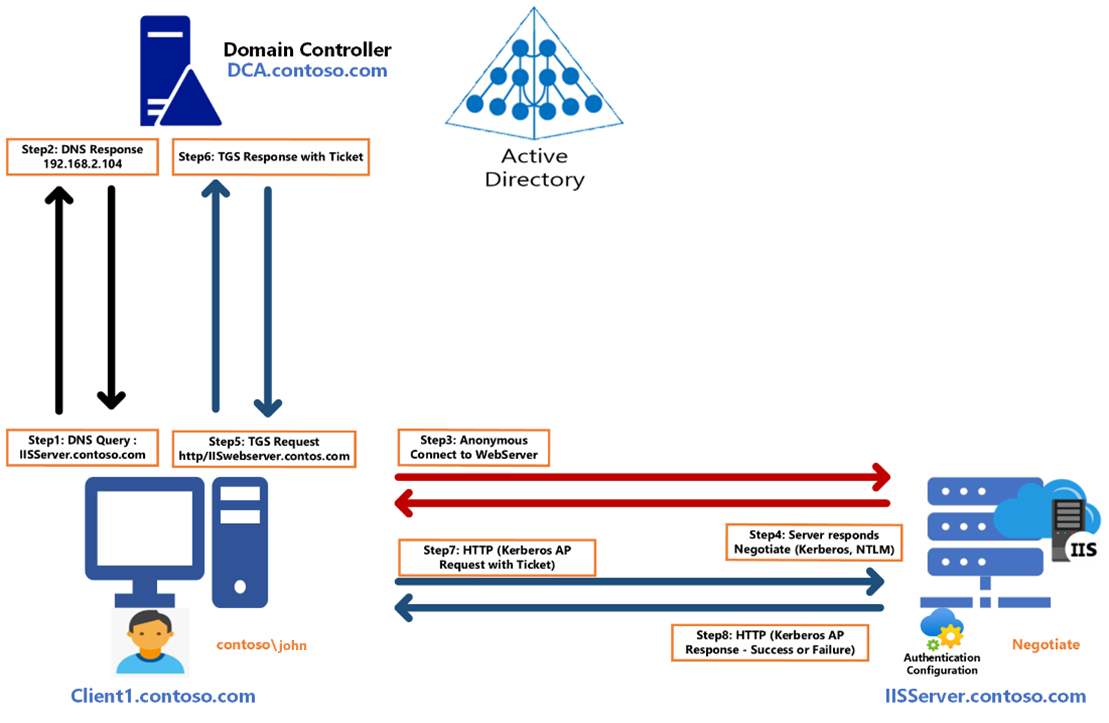
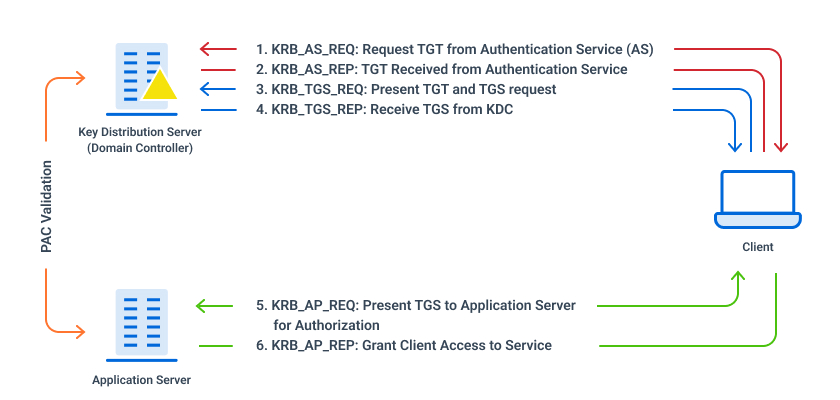
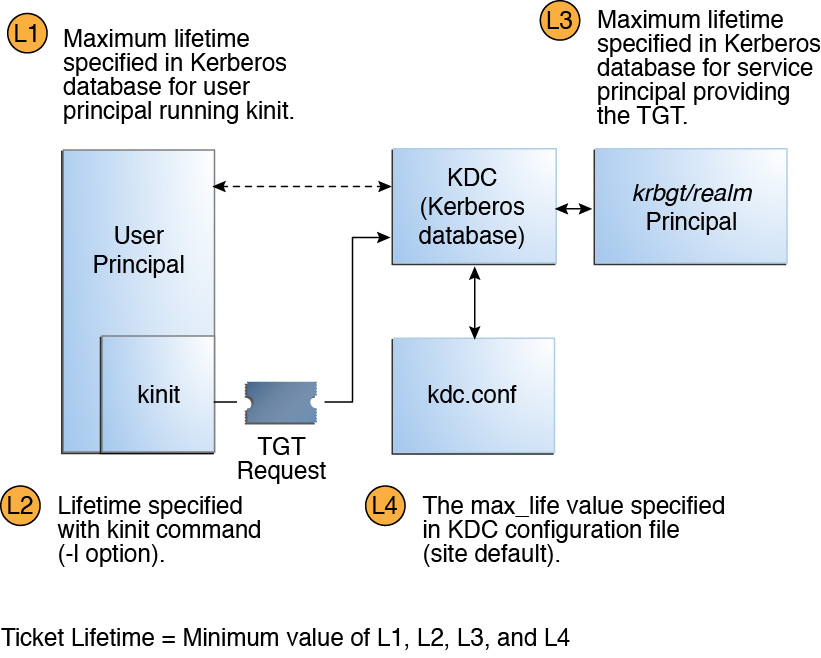
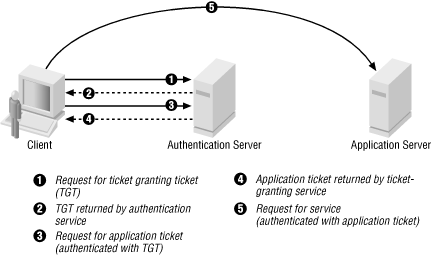
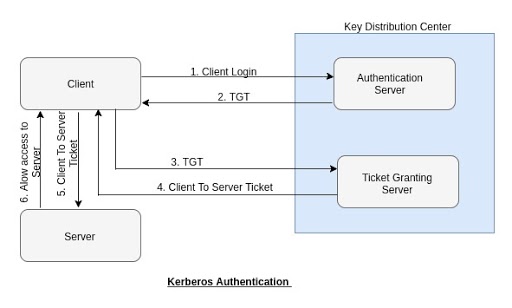
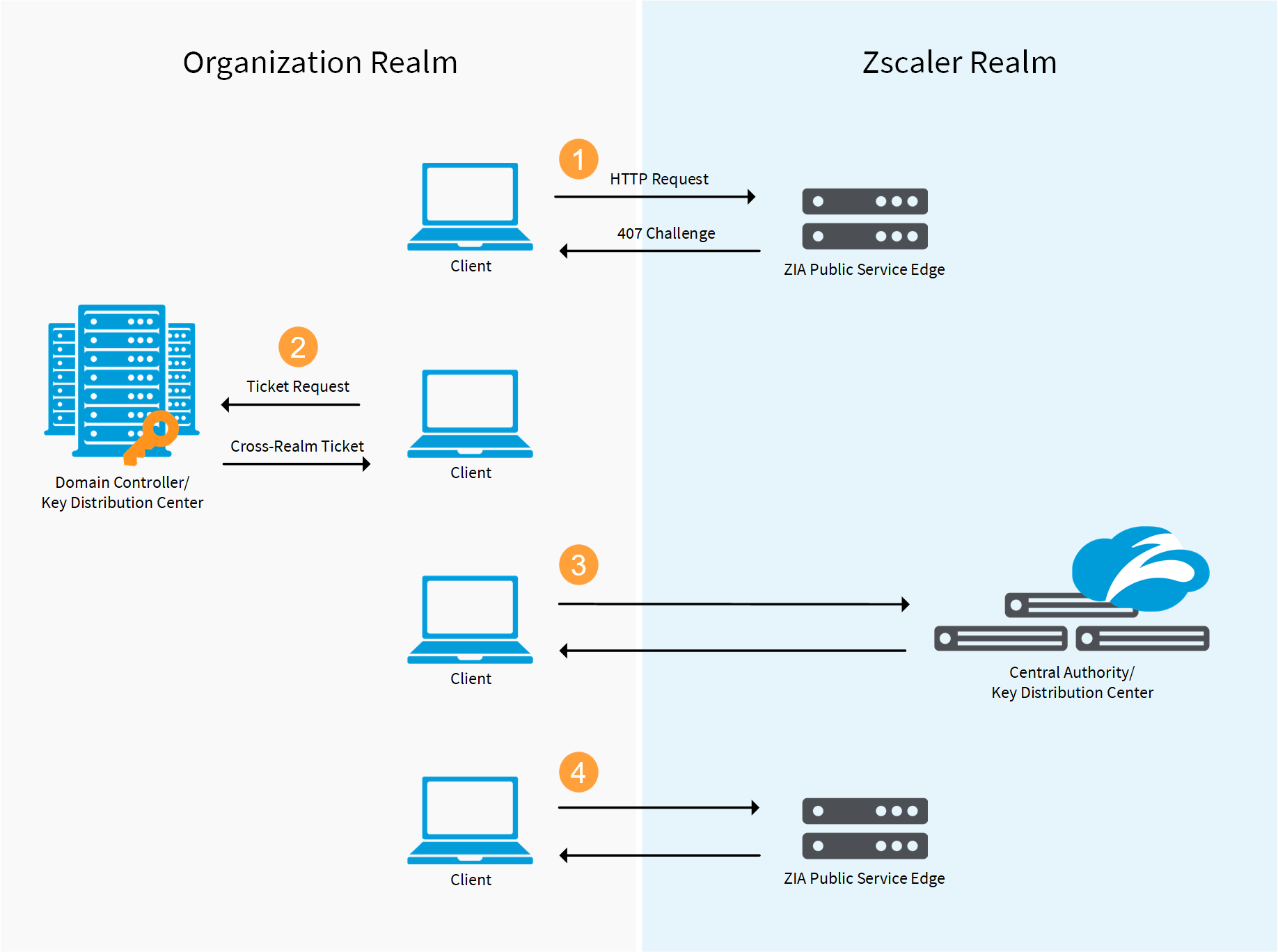
Enabling Kerberos authentication - Asset Reliability | AssetWise APM Wiki - Asset Reliability | AssetWise APM - Bentley Communities
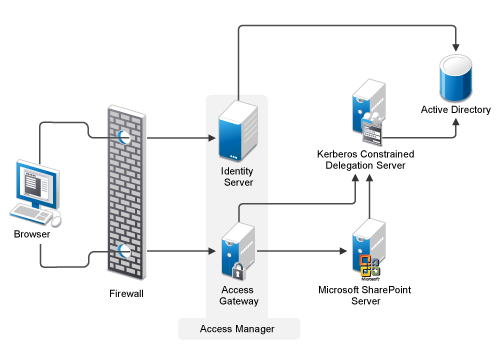
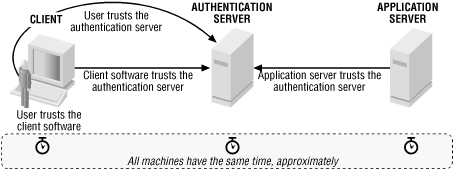
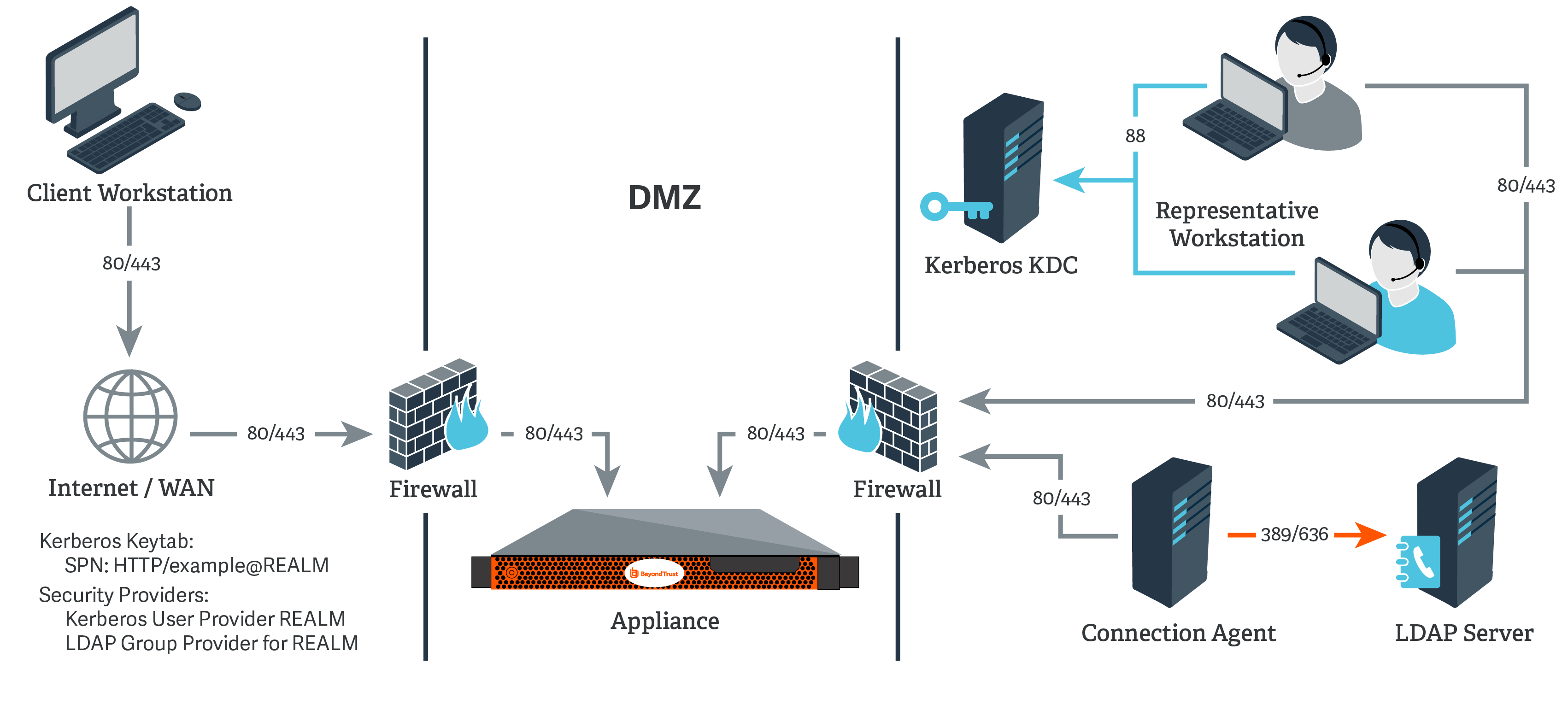
Protecting Kerberized Resources with Kerberos Constrained Delegation - Access Manager 4.5 Administration Guide

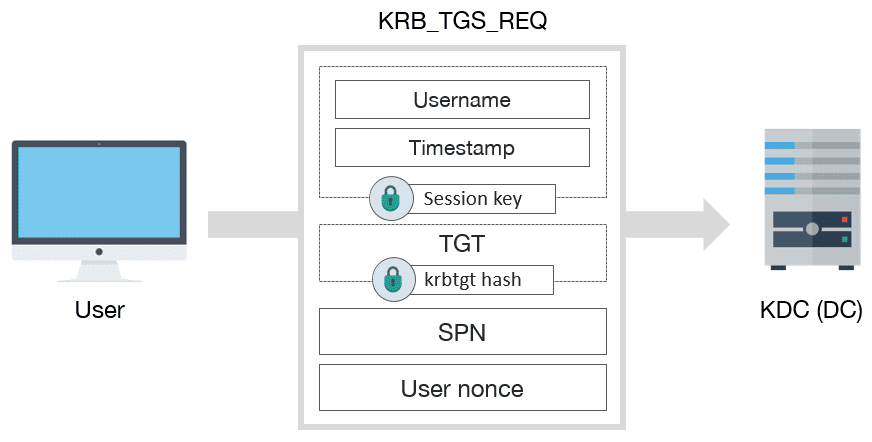
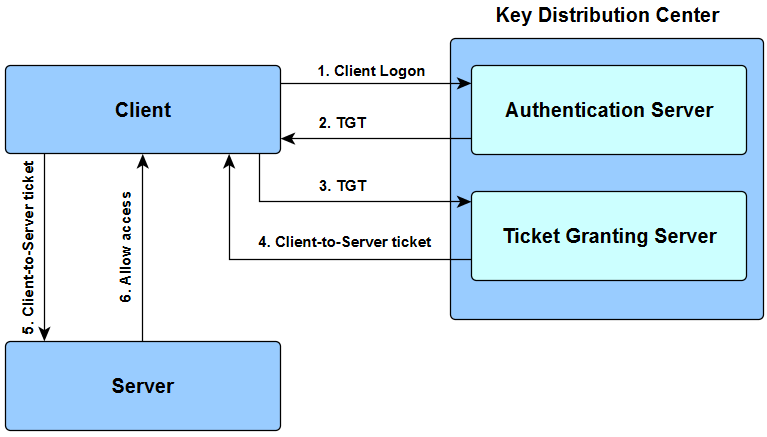
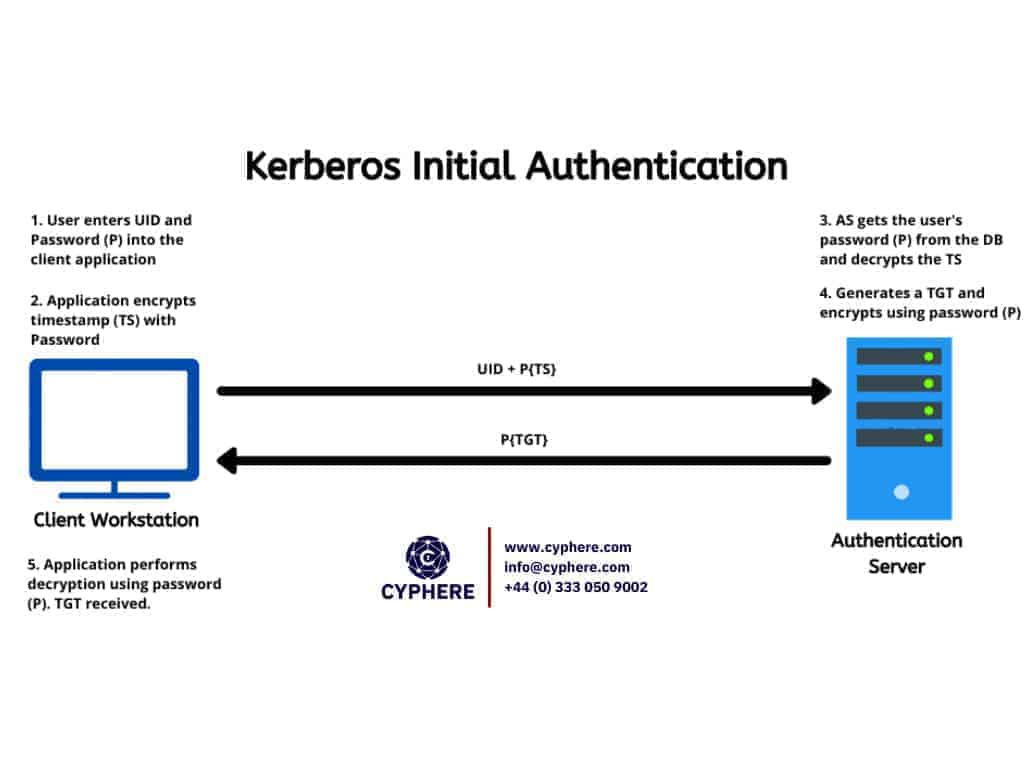
Adding Kerberos realms for discovery authentication - Documentation for BMC Helix Discovery - BMC Documentation